Implementing Historian Security
Implementing Historian Security
Historian is a high performance data archiving system designed to collect, store, and retrieve time-based information efficiently. By default, access to these Historian archives, tags, and data files is available to any valid operating system user account. In this default environment, all users are allowed to read, write, change, and delete archives, tags, or data files in the Historian Administrator, SDK, Migration Tools, and Excel Add-In. However, you may find that you want to make these functions and data available only to authorized personnel. You can do this by creating and defining Historian Security Groups in your Windows Security.
Historian includes an Electronic Signature and Electronic Records security feature. This option provides installations concerned with the FDA's 21 CFR Part 11 regulation or any site interested in added security or tracking the ability to require a signature and password every time a change in data or configuration is requested. For more information on the Electronic Signature and Electronic Records feature, refer to the Using Historian in a Regulated Environment section of the Using the Historian Administrator manual.
To ensure a secure environment when using Historian security, do not create any local user accounts unless Historian is set up on a standalone machine.
Whether or not you use Historian security, make sure that you disable Guest accounts on your computer to limit access to valid Windows user accounts.
About Protecting Your Process
- Modifying data using the Excel Add-In
- Updating security for individual tags or groups of tags
- Creating, modifying, and removing tags
- Tag protection (adding, modifying, removing, and so on) can be applied at a global level to all tags or at the individual tag level.
Refer to Implementing Tag Level Security for more information.
- Reading data in the iFIX Chart object, Excel Add-In, and Migration Utilities
- Writing data
- Starting and stopping collectors
- Creating and deleting collectors
- Creating, modifying, and deleting archives
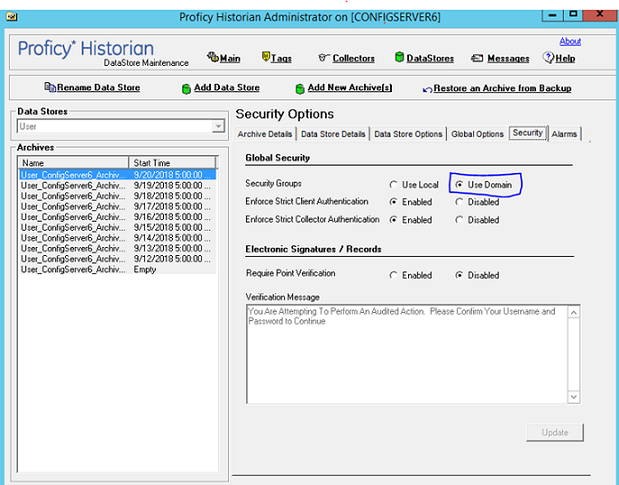
Historian uses the operating system security groups to create a security structure. You enable security for a particular set of functions by adding specific Historian Security Groups to your groups. You can also add security groups to your domain controller. Refer to the Security Tab section in the Historian Administrator Manual for information on selecting local or domain security groups.
By defining one or all of the groups, you begin to set up a security structure. Refer to the Historian Security Groups section for more information on the Historian Security Groups available.
Strict Authentication
With Historian's strict user account authentication features, Enforce Strict Client Authentication and Enforce Strict Collector Authentication, you can control access to the Historian server and safeguard user account credentials.
With strict authentication enabled, only known user accounts configured on the Data Archiver server computer will be able to access a Historian server. Similarly, enabling strict collector authentication enforces the same requirement for incoming collector connections.
For an account to be known at the Data Archiver, it has to exist on that archiver as a local account or exist on a Domain Controller available to the data archiver. Historian will access the local accounts or Domain Controller via Microsofts Security Support Provider Interface (SSPI) and this involves having a Kerberos server setup optionally to assist in account validation.
By default, strict client and collector authentication is enabled on new installations to maximize security. When upgrading from a previous version of Historian, strict client and collector authentication is disabled to allow compatibility with older clients or collectors that cannot be upgraded concurrently.
It is recommended that all clients and collectors receive timely upgrade to the latest version, which permits enabling both strict client and collector authentication on the server for the highest security configuration.
By treating clients and collectors separately, it is possible to accommodate new and legacy authentication during the upgrade process. However, upgrading all clients and collectors to the latest version immediately will achieve a high level of security. The two options, Enforce Strict Client Authentication and Enforce Strict Collector Authentication, permit flexibility during the upgrade process by selectively accommodating legacy clients and collectors.
Strict Authentication Options
This table provides guidelines about the different combinations of strict client and collector authentication options and their use:
| Strict Client Authentication | Strict Collector Authentication | Comment |
|---|---|---|
| Enabled | Enabled | Use this for highest available security. You will need to install SIMs, if available on all pre-6.0 collectors and clients. Clients can refer to any program that connects to the Data Archiver. This includes Historian Administrator, Microsoft Excel, any OLEDB program, user written programs, or any other Proficy software. |
| Enabled | Disabled | Use this if you are unable to upgrade collectors to the latest version if there is no SIM update for your collector. |
| Disabled | Enabled | Use this if you have to support legacy clients and you are unable to install the SIM update on all clients. |
| Disabled | Disabled | Use this for maximum compatibility with existing systems. |
For more information, refer to the product IPI (Important Product Information) ebook or SIM release notes.
Disabling Strict Client and Collector Authentication
To permit older versions of clients and collectors to access a Historian 7.0 (or later) server, disable strict client and collector authentication.
Trusted Connections in Distributed Historian Service Environment
If you want to work in the workgroup setup, contact Online technical support & GlobalCare:www.digitalsupport.ge.com.
Security Strategy Guidelines
- If you disabled the Guest account, a user must provide a valid username and password even if no groups are created.
- Protection is only provided for the functional areas for which you have built the associated Historian Security Groups.
- If you only choose to define some of the security groups, all users still have all access to any uncreated groups. All users are still assumed to be a member of a group unless that group has been created, with the exception of iH Audited Writers group. You must add the iH Audited Writers group to the Windows security groups so that a user can become a member of this group.
For example, if you elect to define the iH Security Admins group and iH Archive Admins group, both the members associated with those defined groups and all other valid users still have access to such functions as creating and modifying tags until you create the iH Tag Admins security group.
- If you implement any Historian Security groups, you must first add and define the iH Security Admins group.
See also Historian Security Groups.
Setting Historian Login Security
ih Security Admins will be checked by the Archiver.For Historian Login Security settings, you can view and set the property from the HistorianSDKsample server properties. The current setting is shown in the data archiver SHW file.
Historian Login Security property is available only in Historian SDK.
To set login security using the Historian SDK:
Historian Security Groups
- iH Security Admins
- Historian power security users. Security Administrators have rights to all Historian functions. This group also has the ability to change tag level security, archive security, and modify the Electronic Records and Signatures option. This is the only Historian security group that overrides tag level security.
- iH Collector Admins
- Allowed to start and stop collectors, browse collectors, configure collectors, and add new collectors.
- iH Tag Admins
- Allowed to create, modify, and remove tags. Tag level security can override rights given to other Historian security groups. Tag Admins can also browse collectors.
iH Tag Admins are not responsible for setting Tag Level Security. This task can only be performed by an iH Security Admins. For more information on setting Tag Level Security, refer to the Implementing Tag Level Security section.
- iH Archive Admins
- Allowed to create, modify, remove, backup, and restore archives.
- iH UnAudited Writers
- Allowed to write data without creating any messages.
- iH UnAudited Logins
-
Allowed to connect the DataArchiver without creating login successful audit messages.
- iH Audited Writers
- Allowed to write data and to produce a message each time a data value is added or changed.
Tag, archive, and collector changes log messages regardless of whether the user is a member of the iH Audited Writers Group.
- iH Readers
- Allowed to read data and system statistics. Also allowed access to Historian Administrator.
Historian Security Group Rights
| Function | iH Security Admins | iH UnAudited Writers | iH UnAudited Login | iH Audited Writers | iH Readers | iH Archive Admins | iH Tag Admins | iH Collector Admins |
|---|---|---|---|---|---|---|---|---|
Create Tags:
|
X | X | ||||||
Remove Tags:
|
X | X | ||||||
Modify Tags:
|
X | X | ||||||
Modify Archive Security:
|
X | |||||||
Backup Archive:
|
X | X | ||||||
Restore Backup:
|
X | X | ||||||
Create Archive:
|
X | X | ||||||
Start/Stop Collector:
|
X | X | ||||||
Browse Collector:
|
X | X | ||||||
Read Data:
|
X | X | ||||||
Write Data (UnAudited):
|
X | X |
X
|
|||||
Write Data (Audited):
|
X | X | ||||||
Modify Data:
|
X | X | X | X | ||||
Update Security for Tag:
|
X | |||||||
Migrate
|
X | |||||||
| Login Connection Messages | X | X | X | X | X | X | X |
Security Setup Example
The following example takes you through the process of establishing your security needs and defining and setting up the levels of security.
| User | Needs | Added to Security Group |
|---|---|---|
| USER1 | Power user. Needs total access to security. | iH Security Admins |
|
USER2 USER3 USER5 USER6 USER8 |
|
|
|
USER4 USER7 |
|
|
| USER9-14 | Read Data. | iH Readers |
Setting Up Historian Security Groups
Creating a Local Group on Windows
To create a new local group:
Adding Users to Windows Security Group
Before adding users to your group, you must first add your users to the Windows system.
To add a user to a group:
Adding a Local User
Adding a Domain User
Active Directory Setup - an Overview
Historian Active Directory setup supports integration with complex models that include the following complexities:
- Users and administrators may belong to different domains within a forest.
- Domains may have sub-domains (multi-level) that need to inherit or refine on inherited permissions
- Group names may be longer than average to cater for group differentiation
The Active Directory setup supports authentication and authorization of users as members of groups from trusted or sub-domains (including assigning appropriate Historian access rights in line with Historian security roles/groups access).
The following figure provides an overview of the Active Directory setup with eamples:
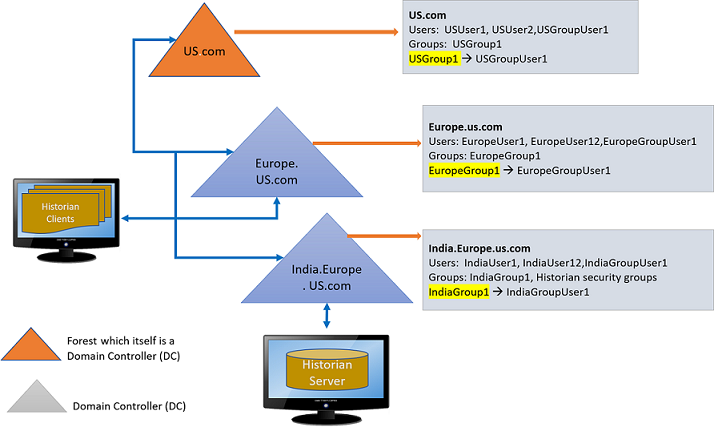
Configuring the Domain Users for active directory setup
To configure the domain (single\multi) environment in the Historian Administrator:
- IH Security Admins
- IH Collector Admins
- IH Tag Admins
- IH Archive Admins
- IH UnAudited Writers
- IH UnAudited Logins
- IH Readers
- IH Audited Writers Note: Historian Security Groups should be of type Domain-Local only.
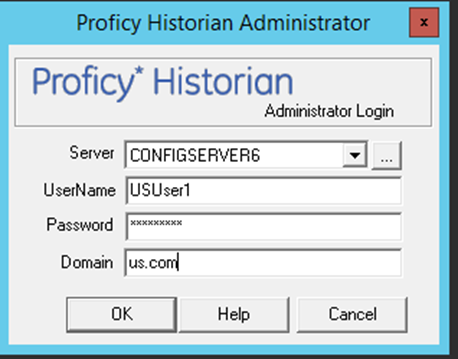
Accessing Historian Server using Domain Users - Examples
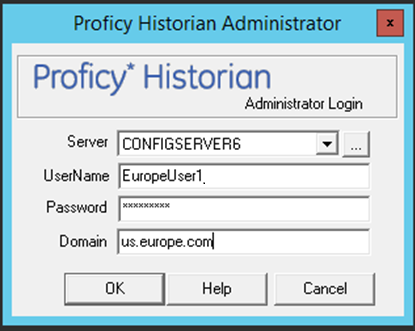
Example 1: European domain user trying to connect to Historian Server installed in India.Europe.US.com Domain Controller (DC).
Adding Nested Domain Groups to Historian Security Groups
The following procedure describes, a European domain group user trying to connect to Historian server, installed in India.Europe.US.com Domain Controller.
Using the UAA Config Tool
- Add a local UAA user.
Here a local UAA user means a user defined by UAA, not by an external identity provider such as LDAP.
- Remove a local UAA user.
- Reset the password for a local UAA user.
- Add a local UAA user to an existing UAA group.
Since OAuth2 scopes are implemented as UAA groups, this means the same as adding a scope to a user.
- Remove a local UAA user from an existing UAA group.
A user who performs these functions is acting as the adminclient and needs to know the secret of the admin client. The tool does provide a way for the user to cache the secret safely to be used later.
The tool is installed in the UAA subdirectory of the Historian installation directory, typically C:\Program Files\GE Digital\UAA. Run the tool from a Windows command prompt window.
Syntax
The tools syntax follows this format:
uaa_config_tool verb [options]add_userremove_userset_user_passwordadd_user_to_groupremove_user_from_groupclear_secret
Run the tool without a verb or any other options to view the help screen.
Options can be specified in the form of single dash followed by a short name, or double dash followed by a long name, followed by the value of the option, if any. For example, you can specify the user name Alice by either
-u Aliceor
--UserName AliceOptions
| Short name | Long name | Remark |
-t |
--Target |
URL of the UAA instance that the command should be performed on. Typically, the URL is https://localhost:8443/uaa, which is the default value. This option is optional and is only needed when the user wants to run the command against a remote UAA instance (which is not recommended due to security concerns). |
-n |
--ClientId |
ID of the client that the user is acting as. By default, it is admin. This option is optional and is only needed when the admin has set up the UAA to delegate certain operations to others. |
-s |
--ClientSecret |
This is the secret used to authenticate the user for acting as the admin client (or an alternative client given in a --ClientId option). If the user has elected to cache the secret previously, then this option can be omitted. Otherwise, it has to be provided. |
-c |
--CacheSecret |
This option is not followed by a value and is optional. If specified, the tool will cache the client secret so when the next time this tool is invoked the secret does not have to be specified. Note that the secret is encrypted and only the current Windows logon user can access and decrypt. |
-u |
--UserName |
Name of the user that the tool is being invoked for. For example, the user that is being added or removed. |
-p |
--UserPassword |
The password for the user being added or whose password is being reset. The option is only needed for the add_user and set_user_password commands. |
-g |
--Group |
Name of the UAA group (scope) that the user is being added to or removed from. The option is only needed for the add_user_to_group and remove_user_from_group commands. |
Examples
- To add a new user named
bobwith the passwordbobcat2(with the admin client secretMyNotSoSecretspecified on the command line, to be cached and used later):uaa_config_tool add_user -u bob -p bobcat2 -s MyNotSoSecret -c - To add user
bobto the grouphistorian_visualization.user, using the previously cached admin secret:uaa_config_tool add_user_to_group -u bob -g historian_visualization.user - To remove user
alicefrom a remote instance of UAA as an alternative client (that is, other thanadmin)useradmin:uaa_config_tool remove_user -u alice -t https://webhost.lab:8443/uaa -n useradmin -s MyOtherNonSecret - To clear any cached client secret:
uaa_config_tool clear_secretNote: If the Windows logon account is not shared, it is not necessary to clear cached secret, since the cache is encrypted and only the same Windows user account can decrypt.
Adding a UAA User
These instructions are for adding users and clients to the UAA server after a non-domain or non-LDAP Historian installation. You must have Internet access on the machine on which you are performing these steps.
About Domain Security Groups
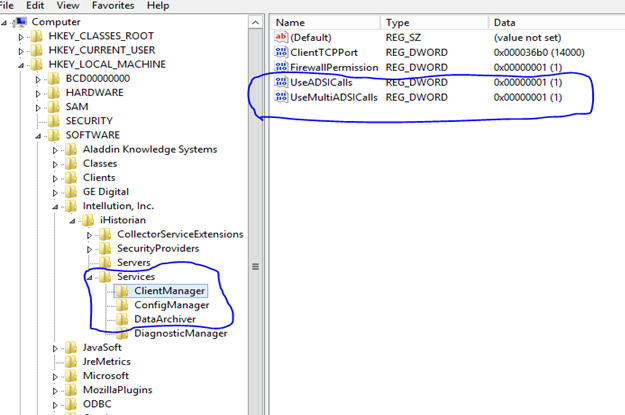
When you configure Historian to use Domain security groups, the Data Archiver attempts to locate the groups on the Primary Domain Controller (PDC) or one of the Backup Domain Controllers (BDC). If you don't have a primary domain controller or if it is slow to access, you can have the Data Archiver access the nearest domain controller via the UseADSICalls registry key. When using a PDC, if a Primary or Backup Domain Controller cannot be located when the Historian Data Archiver service starts, access to Historian is denied to all users.
For troubleshooting, the data archiver show (.SHW) file lists all PDCs and BDCs available at the time of archiver startup. Use this list to verify that the Historian Server has visibility into the appropriate domain.
When using a PDC, after the list of Domain Controllers has been established, the Historian Server will use that list to query for Security Group Membership on an as needed basis. If at any time a request for Group Membership information is made and the Primary Domain Controller is not available, Historian selects the first Backup Domain Controller and attempts the same request. If a Backup Domain Controller successfully responds to the request, the process of querying for Group Membership can stop. Otherwise, Historian will attempt to query Group Membership information from the next available Backup Domain Controller. If no Backup Domain Controller successfully responds, access to the system is denied.
When using the UseADSICalls registry key, Historian does not connect to a specific domain controller and lets the operating system contact the most available one.
Changing security group configuration from Local to Domain or vice versa requires that the Historian Data Archiver service be restarted for the change to take effect.
Creating a Global Security Group in a Windows 2003 Domain
Creating a Security Group in a Windows 2008 Domain
Using a Windows 2003 Domain Controller with a Windows 2008 Historian Server
Act as a Part of the Operating System to its list of rights.- Set up the log-on of the Historian data archiver service:
- Add the
Act As Part of Operating Systemright to the domain account:
Configuring Data Archiver to use Active Directory Service Interface
With the Active Directory Support feature, you can configure the Data Archiver to use a different set of Windows calls called Active Directory Services Interface (ADSI) when using Historian security. Configuring the Data Archiver to use Active Directory Services Interface (ADSI) allows you to:
- Log in to the Historian even if the Data Archiver is unable to enumerate any domain controllers during the Data Archiver startup.
- Access a Backup Domain Controller if a Primary Domain Controller is not available temporarily or permanently.
You should configure the Data Archiver to use Active Directory Services Interface (ADSI) only when the Data Archiver fails to enumerate domain controllers.
Security Settings
=================
Group Mode : GLOBAL
Use Client Windows User for Logon : TRUE
Security Domain : <your domain>
Group Server #01 : The following procedures provide guidelines for configuring the Data Archiver to use Active Directory Services Interface (ADSI) calls.
Creating a Registry Key and Turning On UseADSICalls
Configuring Data Archiver to use Active Directory Service Interface
With the Active Directory Support feature, you can configure the Data Archiver to use a different set of Windows calls called Active Directory Services Interface (ADSI) when using Historian security. Configuring the Data Archiver to use Active Directory Services Interface (ADSI) allows you to:
- Log in to the Historian even if the Data Archiver is unable to enumerate any domain controllers during the Data Archiver startup.
- Access a Backup Domain Controller if a Primary Domain Controller is not available temporarily or permanently.
You should configure the Data Archiver to use Active Directory Services Interface (ADSI) only when the Data Archiver fails to enumerate domain controllers.
Security Settings
=================
Group Mode : GLOBAL
Use Client Windows User for Logon : TRUE
Security Domain : <your domain>
Group Server #01 : The following procedures provide guidelines for configuring the Data Archiver to use Active Directory Services Interface (ADSI) calls.
Restarting the Data Archiver Service
Establishing Your Security Rights
Implementing Tag Level Security
Set tag level security in the Historian Administrator. You do not need to use the Historian Security Groups for this security setting. You can use a Windows pre-defined group (power users, for example) or create your own separate group specifically for this function. For more information on creating and adding groups, refer to Setting Up Historian Security Groups.
Users must have iH Security Admins rights to set individual tag level security, browse, or query tags in the Historian Administrator.